In answer to the question - what have I been writing about? I found that I wrote about a myriad of topics from security breaches to certifications. However, while all of them were different – they all had something in common – the information highway can be a scary place and you need to have controls in place to ensure a smoother ride!
Week1 - Passing the Buck - Who's responsible for the security breach? - My first blog discussed a major security breach at a market that involved over 2 million credit and debit cards being compromised. I discussed how long it took the company to notify their customers and how that breach also involved several other entities.
Week2 - One Billion Served! – I thought my initial post was a little boring so I actually started to let my creative side take over and included graphics and charts to help spruce up my post! This post described the number of smartphone and tablet owners and how we need to improve security measures for these types of devices.
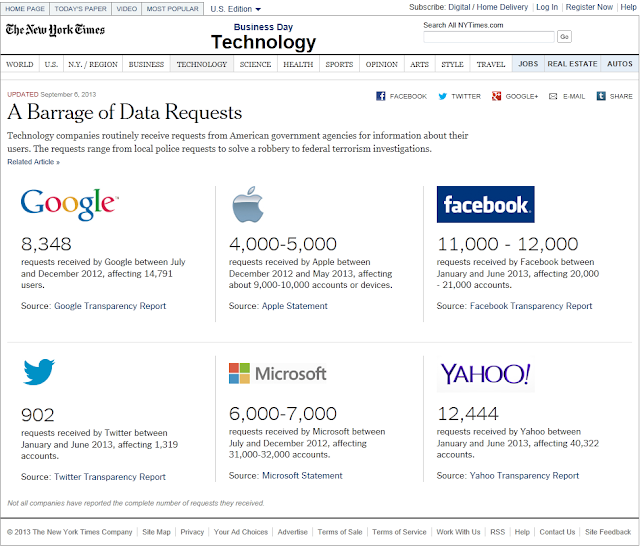
Week3 - Shhhhh....Don't tell anyone! – I concentrated this week's blog on the recent NSA scandal. I find it frightening how the government is entwined in all we do online. In six months Facebook had received over 12,000 requests for customer information from various government agencies – really makes me think twice before I post something.
Week4 - BACKUP - It's Gonna Blow! – This week's blog was focused on the importance of a business having both Disaster Recovery and Business Continuity plans in order to mitigate the risk of a disaster. I also found a funny cartoon that I posted:
Week5 - Press the Key for Security... – This blog discussed the importance of developing a security plan and the steps necessary to accomplish this. I also found this quote which summed up the discussion for me "Security in IT is like locking your house or car – it doesn't stop the bad guys, but if it's good enough they may move on to an easier target." — Paul Herbka
Week6 - Security Starts With You! – This was an interesting blog for me. I wanted to show how important you are to the role of security. In addition, I wanted to emphasize the importance of security training and awareness and how it fits into the company culture. I also found a hilarious youTube video of a product called the Password Minder that Ellen Degeneres featured on her show. It was a ridiculous product that was nothing more than a notebook to hold all of your passwords in. It is very funny!
Week7 - ISO 27K What? – I created this blog dealing with the ISO 27K process because I wanted to find out more about the process. I really hadn't realized all that goes into this certification for companies and it gave me a better appreciation for those organizations that do invest the time, money, and personnel to implement these standards.
Week8 - IT can be a RISKY Business! – The focus of this week's blog was on the importance of Risk Management in information technology. Defining risks and developing a risk management plan should be a part of any IT initiative and I hope this blog reflected that. Of course I did have a little help from Albert Einstein in trying to get my point across - "Everything that can be counted does not necessarily count; everything that counts cannot necessarily be counted" - Albert Einstein.
Week9 - Is it Worth the Risk? – This blog put an emphasis on the cost benefit analysis side of risk management. I did find some great tutorials that discussed the idea of CBA located at this link: Cost Benefit Analysis
Week10 - Things That Go BUMP in the Night.... – Since I love all things scary and it was Halloween week – I decided to create a blog dedicated to the "scary" side of computing such as: Viruses, spoofing, Denial of service attacks, malware, social engineering, and zombie attacks! I discussed the Sphere of Protection and how it might help to protect your company against these types and other types of threats.
Week11 - Certifications - Are They the Necessary Evil? - This week's blog addressed the question of certifications – are they necessary? While there doesn't appear to be a simple answer – I did realize this after my research – education can never hurt your chances of succeeding. So if you have the ability and time – adding certs to your resume will not hurt.
I definitely feel that these types of blogs are useful to information security professionals and really any information technology professional – it gives you a chance to research and see what is happening out there now. Textbooks are fine – but technology is constantly updating and it's difficult to grasp some of that in a textbook alone. The internet can be a great tool for learning.
Lessons learned: Make sure you verify your information. Also – use graphics, videos, and charts to keep your posts interesting. I found it easier for me to convey my thoughts in this fashion. Last – have some fun with it!